In today’s digital world, where our lives are entwined with smartphones, mobile app security has never been more vital. Consider your apps as digital fortresses that protect sensitive data.
This article is your key to strengthening these digital defenses. We’ll journey through the significance of industry best practices, like OWASP, NIAP, CWE, and CVSS, to shield your data and ensure a worry-free mobile experience.
Read on and learn more about the top security practices that will make your mobile experience seamless and safe.
The overflow of threats and attacks on mobile apps has made businesses more concerned than ever about keeping their users safe and secure. Even the apps that were deemed to be secure and impenetrable are now being crept into with severe vulnerabilities. And this is why we made a huge priority shift toward mobile app security.
Moreover, when seeking viable solutions to promptly identify code defects and vulnerabilities in mobile apps, we here at ThinkPalm adhere to major mobile app security standards. We choose the best selection strategy tools based on industry-leading guidelines and standards such as OWASP, NIAP, CWE, and CVSS.
In the next step, the lead development team checks whether the production-ready build meets the testing and security requirements established by the OWASP Mobile Top 10 before rolling it out to market.
Millions of people use the OWASP Mobile Top 10 as a baseline for mobile app security, and it assists security and development teams in finding and mitigating vulnerabilities earlier in the development life cycle, improving the quality of their code, and minimizing security flaws before deployment and production.
This primary mobile app security standard covers all important security categories like reverse engineering, authorization, authentication, quality of code, security of data at rest and in motion, etc. All of these factors are ensured to be on our development team’s security checklist.
Once the application OWASP security practices are compliant, the app has to go through Common Vulnerability Scoring Systems (CVSS). It’s the most widely recognized standard for rating the severity of application vulnerabilities and determining the urgency of mitigation.
Further, this scoring system is utilized by the team as a security tool to review the severity of detected vulnerabilities and determine the course of action. CVSS produces a numerical score highlighting risk severity by capturing the key features and characteristics of the vulnerability.
This score will then be translated into categories like low, high, or medium, and based on this, the security teams will decide and prioritize their next steps and boost their remediation and vulnerability management measures.
As a team, we abide by the following critical practices when building secure mobile apps:

DexGuard provides multiple layers of source code encryption and obfuscation. As most of the code in a native mobile app is on the client side, mobile malware can easily track the bugs and vulnerabilities within the source code and design. Attackers generally repack renowned apps into rogue apps using reverse-engineering techniques. Then, they upload those apps into third-party app stores with the intent to attract unsuspecting users.
Threats like these can take your organization’s reputation downhill. Developers will be careful while building an app and include tools to detect and address security vulnerabilities. Developers will ensure their applications are robust enough to prevent tampering and reverse engineering attacks. Encrypting the source code will be done to defend the application from these attacks as it ensures it is unreadable.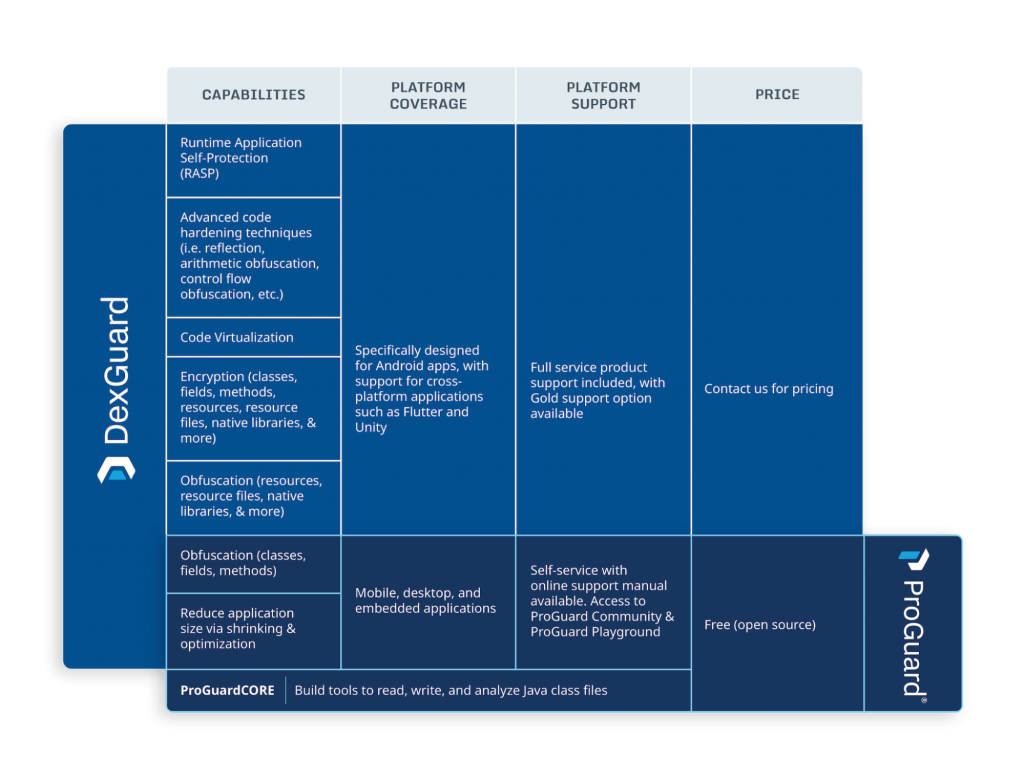
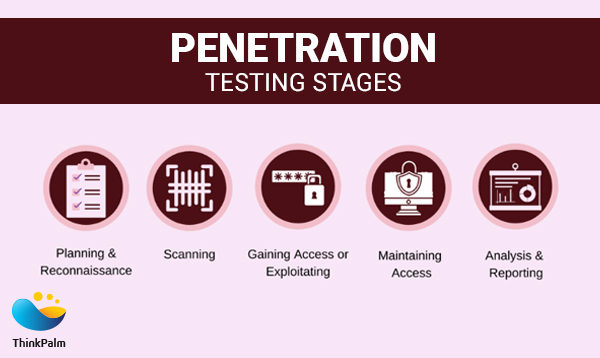
The team consistently tests the application against randomly generated security scenarios before every deployment. In particular, pen testing will be performed to avoid security risks and vulnerabilities against the mobile apps and to detect loopholes in the system, which is an absolute necessity since these loopholes could grow to become potential threats that give access to mobile data and features.
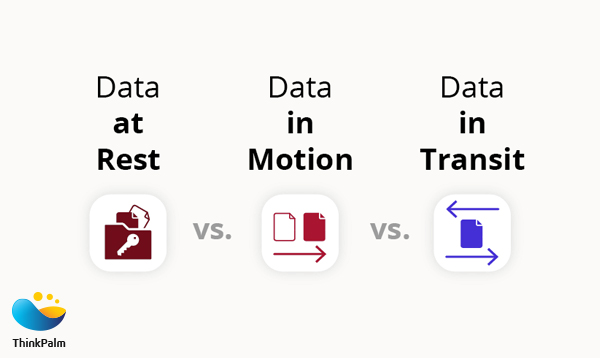
The sensitive information that is transmitted from the client to the server will be protected against privacy leaks and data theft. We use either an SSL or VPN tunnel, ensuring user data is protected with strict security measures. Also, as an added security layer, apps implement Certificate pinning, the practice of restricting the certificates that are considered invalid for the app to those that have previously been authorized. Certificate pinning is done by providing a set of certificates by the hash of the public key (SubjectPublicKeyInfo of the X.509 certificate).

The data in the mobile app sandbox are not effectively encrypted; hence, there is a major loophole for potential vulnerabilities. To ensure security in the sandbox environment, we implement mobile app data encryption using SQLite Database Encryption Modules or practice file-level encryption across multiple platforms.
Popular cryptography algorithms like MD5 and SHA1 often fail to meet the ever-increasing security requirements. The team will ensure to be updated with the latest security algorithm, and whenever possible, we use modern encryption methods like AES with 512-bit encryption, 256-bit encryption & SHA-256 for hashing. In addition, QA performs manual penetration testing and threat modeling on the applications before they go live to ensure foolproof security.
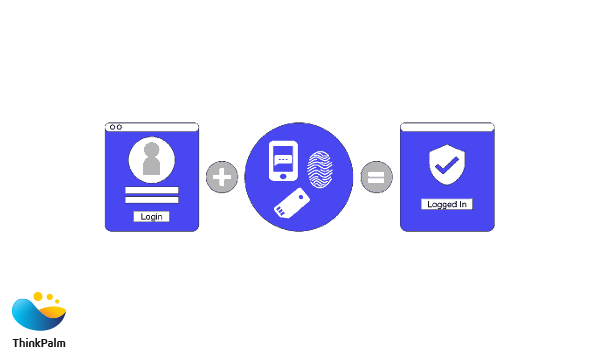
In order to prevent security breaches, developers design the apps in such a way that they only accept strong alphanumeric passwords. On top of that, we make it mandatory for the users to change their passwords periodically. For extremely sensitive apps, we strengthen the security with biometric authentication using fingerprint. Encouraging the users to ensure authentication would be the recommended way to avoid security breaches.
The majority of mobile applications we build here have a client-server mechanism. So, we grab the essential to have security measures in place to safeguard against malicious attacks at backend servers. The team verifies all the APIs in accordance with the mobile platform that it aims to code for because API authentication and transport mechanisms can deviate from one platform to another.
 When sharing data between two apps you control or own, use signature-based permissions. These permissions don’t require user confirmation and, instead, check that the apps accessing the data are signed using the same signing key. Therefore, these permissions offer a more streamlined, secure user experience.
When sharing data between two apps you control or own, use signature-based permissions. These permissions don’t require user confirmation and, instead, check that the apps accessing the data are signed using the same signing key. Therefore, these permissions offer a more streamlined, secure user experience.
When requesting credentials from users to access sensitive information or premium content in your app, ask for either a PIN/password/pattern or a biometric credential, such as face recognition or fingerprint recognition.
Request only the minimum number of permissions necessary for your app to function properly. When possible, relinquish permissions when your app no longer needs them.
If your app uses data from external storage, make sure that the contents of the data haven’t been corrupted or modified. Include logic to handle files that are no longer in a stable format.
Most apps use external libraries and device system information to complete specialized tasks. By keeping the app’s dependencies up to date, we make these communication points more secure.
Root checking will check if the device is rooted by checking if the device has Superuser privileges. Identifying the device’s state allows the app to decide whether to continue functioning or prevent users from accessing app features.
The app has to protect against security threats with SafetyNet provided by Google. SafetyNet provides a set of services and APIs that help protect your app against security threats, including device tampering, bad URLs, potentially harmful apps, and fake users. It also allows to identify the source of app installation.
In the dynamic realm of mobile app development, ThinkPalm leads the way with expertise in Flutter, React Native, and other top robust tech stacks. Specializing in IoT, OTT, Maritime, and E-commerce, our custom app development process ensures your seamless journey from idea exploration to market deployment. Guided by our expert developers, we prioritize secure, production-ready apps, adhering to industry standards like OWASP.
Moreover, meticulously scrutinizing code, we fortify your app against rising threats, guaranteeing a transformative experience on platforms like Android, iOS and cross-platform solutions. Experience excellence with ThinkPalm’s Mobile Application Development Services—your gateway to secure, intuitive, and market-ready apps. Book a FREE consultation to embark on a transformative mobile app journey with ThinkPalm.