In the digital world, where businesses rely heavily on software and websites, the first line of defense is ‘security testing.’
As the saying goes, ‘One Single Vulnerability Is all An Attacker Needs.’ ‘Be Secure and Protect Your Data.’
Moreover, for the same reasons we lock our houses and valuables for their safety in the physical world, our businesses and customers must do the same in the digital world.
Now, it’s more important than ever since cyber threats are rising.
In this blog, we will explore the amazing tools and best practices we use at ThinkPalm to ensure everything stays safe online. Let’s jump in!
What Is Security Testing?
Security testing is like checking a car before it hits the road.
We want to ensure it’s in the best possible condition.
In the digital world, we do the same for software and websites.
We look for any weak points that could be trouble, like easy-to-guess passwords or parts of the system that aren’t set up quite right.
But here’s the fun part: we don’t wait until the software is live for everyone to use.
We do this check while it’s being built, just like inspecting a bridge before cars drive on it.
This way, we catch and fix problems early before they cause any potential harm.
It’s like making sure your home is safe and secure before anyone tries to break in.
That’s why security testing is so important.
Why Security Testing Really Matters?
Have you ever wondered why we do security testing?
Here are some key reasons:
- Spotting Hidden Threats: Think of security testing as a digital detective. It helps us find potential threats lurking in our systems.
- Hunting for Weak Spots: We use security to find vulnerabilities, threats, and risks in apps and websites. Moreover, it’s like finding weak spots in a fortress.
- Helping Developers Build Safely: Security testing is like a guide for developers. In addition, it shows them how to make their code secure while they’re building it.
- Detecting Issues Early: We believe in finding security problems as soon as possible, like finding a small leak before it floods the whole house.
- Tools for Everyone: We ensure all developers can use security tools, like giving everyone a shield to protect their work.
- Preventing Future Troubles: By tackling security issues before we finish and release our software, we ensure a smoother journey without unexpected storms later on.
Major Security Testing Tools We Use At ThinkPalm
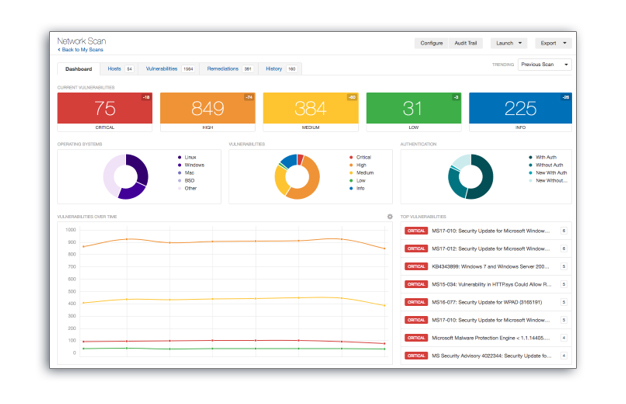
1. Tenable One
Let’s take a closer look at some of the key security testing tools we use at ThinkPalm:
Tenable One is an open-source security tool designed to manage and monitor exposure to potential threats continuously.
Moreover, its mission is to provide organizations with a clear view of their attack surface, empower them to thwart potential attacks and enable them to assess and communicate exposure risk effectively.
Here’s how it works:
- Comprehensive Scanning: It checks for vulnerabilities in everything from devices and apps to operating systems and cloud services.
- Patch Detection: Tenable One spot security gaps and missing patches.
- Daily Monitoring and Updates: We use it daily to monitor our systems, ensuring they are up-to-date and secure.
- Efficient Handling: Tenable One can handle multiple projects and branches simultaneously, making our security efforts seamless.
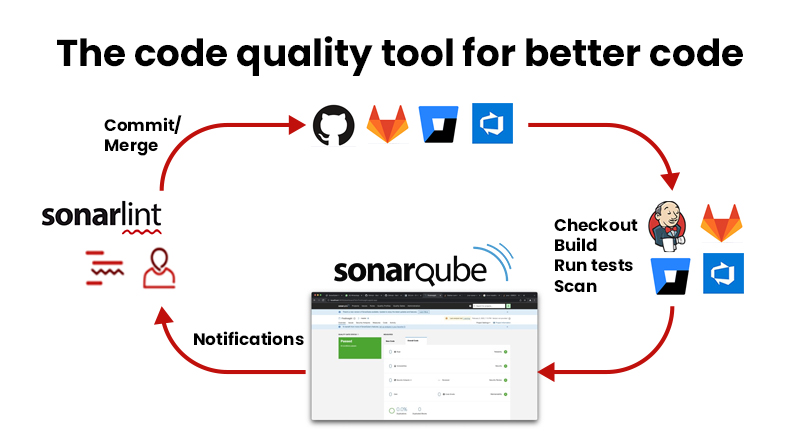
2. SonarQube
SonarQube is an open-source tool that serves as a static code analyzer focused on enhancing security in software development.

It supports all programming languages used in our product, and We can integrate Sonarqube with the CI/CD pipeline.
Here’s how it works:
- Code Quality Assurance: SonarQube acts as a Code Quality Assurance Tool, collecting and analyzing source code to provide reports on code quality. Moreover, it actively detects security issues and vulnerabilities in code.
- Universal Applicability: It applies to every developer contributing code to our projects.
- Daily Monitoring: We monitor SonarQube daily. If new code commits introduce security issues or vulnerabilities, we promptly flag these to developers through Jira. Additionally, if there are false positives, we can address them by adding explanatory comments in the SonarQube dashboard.
- Continuous Scanning: A daily Jenkins job scans team branch commits, making new code issues visible in SonarQube.
- Issue Tracking: We’ve raised numerous bugs to developers through Jira based on SonarQube findings, aiming to resolve them.
Coverage of 7 Sections of Code Quality
- Architecture and Design: SonarQube assesses the architectural and design aspects of the code to ensure it follows best practices.
- Unit Tests: It checks for the presence and effectiveness of unit tests to verify code functionality.
- Duplicated Code: SonarQube identifies and helps eliminate duplicated code segments, improving code maintainability.
- Potential Bugs: The tool detects potential bugs in the code, enabling developers to address them before they become critical issues.
- Complex Code: It assesses the complexity of the code, promoting the development of more straightforward and maintainable code.
- Coding Standards: SonarQube enforces coding standards and best practices to ensure consistent, high-quality code.
- Comments: It assesses the code’s presence and quality of comments, promoting better code documentation.
Features and Advantages of Using SonarQube
SonarQube offers several features and advantages, including:
- Increased Software Lifetime: SonarQube significantly increases the lifetime of applications by reducing complexities, eliminating duplications, and identifying potential bugs in the code. Therefore, this results in a cleaner and more robust code architecture and increased unit tests, enhancing the longevity of the software.
- Improved Maintainability: By continuously monitoring code quality and addressing issues early, SonarQube improves the maintainability of the software. Developers can work more efficiently on clean and well-structured code.
- Change Handling: SonarQube has the ability to handle changes effectively. It helps identify and manage code issues introduced by changes, ensuring that the software remains reliable and secure throughout its lifecycle.
Benefits of SonarQube
Using SonarQube provides several key benefits, including:
- Sustainability: SonarQube reduces complexity, identifies possible vulnerabilities, and eliminates code duplications, ultimately optimizing the lifespan of applications. It helps ensure that software remains sustainable and secure over time.
- Increased Productivity: By reducing the scale of issues, lowering the cost of maintenance, and mitigating the risk of the application, SonarQube boosts developer productivity. It reduces the need to spend excessive time making code changes and fixes, allowing teams to focus on adding new features and functionality.
Dashboard
3. Nmap Tool
Nmap, the open-source network scanning tool, is a powerful asset in our toolkit.

It helps us manage our network effectively by discovering devices, finding open ports, and identifying vulnerabilities. Here’s an overview of how it works and the key scan types:
Tool Overview:
- Device Discovery: Nmap assists us in finding devices operating on our network.
- Port Detection: It discovers open ports and services running on those ports.
- Vulnerability Detection: Nmap helps us identify potential vulnerabilities in our network.
Scan Types:
- TCP Scan: We use this when we need a detailed analysis of a host. TCP scans are thorough and use a connection-based protocol.
Command: sudo nmap -sT -T4 -Pn -p1- <host>
- UDP Scan: For faster results and to detect open UDP ports, we opt for UDP scans. Also, since UDP is a connectionless protocol, it makes this scan quicker.
Command: sudo nmap -sU -T4 -Pn –max-retries 2 -p1- <host>
- Service Scan: This scan type helps us identify the services running on a host. Moreover, It’s vital for understanding the software and versions in use, which is crucial for security assessments.
Command: sudo nmap -sV -T4 -Pn -p1- <host>
Broad Capabilities of Nmap
Here’s a breakdown of the primary uses and capabilities of Nmap:
- Scan Every Active IP Address: Nmap enables you to gather detailed information on every active IP address on your network to determine whether an IP has been compromised. The Nmap tool will let you know whether the IP address is being used by a legitimate service or by an external hacker.
- Perform Entire Network Scanning: Nmap provides comprehensive information about your entire network, including a list of live hosts, open ports, and the operating system of every connected device. Due to this, Nmap does an excellent job at monitoring your ongoing system and helping perform pen-testing.
- Identify the Vulnerabilities of the server: You can use the Nmap tool to scan your web server for any security breaches or gaps to protect personal and business websites. Also, Nmap helps simulate the process a malicious agent typically uses to attack your website.
- Develop Visual Mappings: Nmap includes a graphical user interface known as Zenmap. You can also use it to build visual mappings of your network to improve usability and reporting.
- Automate System and Vulnerability Scans: Nmap has an incredible “Nmap Scripting Engine” (NSE) feature. It’s a scripting engine that lets you use a predefined set of scripts and automate networking features.
Penetration Testing (Pen Testing)
Penetration Testing, or Pen Testing for short, is another crucial security testing method used to identify vulnerabilities, threats, and risks in software applications, networks, or web applications. It’s like having ethical hackers simulate attacks to discover security weaknesses that need fixing.
Here’s the basic idea:
- Purpose: We do it to find and fix security issues in our software.
- Ethical Hacking: We have friendly hackers who try to break into our systems to see if they can find any weaknesses.
- Part of Security Strategy: Pen Testing is important to our overall security plan.
Although pen testing is mostly manual, pen testers use automated scanning and testing tools.
They not only utilize tools but also apply their knowledge of the latest attack techniques to perform more comprehensive testing than what a vulnerability assessment, primarily relying on automated testing, can offer.
Manual Pen Testing
Manual penetration testing goes beyond the scope of popular vulnerability lists like the OWASP Top 10.
It identifies vulnerabilities and weaknesses that automated testing may miss, particularly in areas such as data validation and integrity checks, which involve intricate business logic.
Additionally, manual penetration tests help in distinguishing false positives that automated testing tools might report inaccurately.
Due to the expertise of penetration testers who emulate adversarial thinking, they can analyze data to tailor their attacks, assessing systems and websites in ways that automated testing solutions cannot replicate.
Automated Testing
Automated testing offers the advantage of producing results more rapidly and requiring fewer specialized professionals compared to a fully manual penetration testing process.
These automated testing tools automatically track results and often allow for easy export to a centralized reporting platform.
In contrast, manual penetration tests can yield varying results from one test to another, while running automated testing consistently on the same system will consistently produce the same results.
Penetration testing, whether manual or automated, is essential to our security strategy. It helps us proactively identify and address security vulnerabilities, ultimately strengthening our security posture and protecting our software, networks, and web applications from potential threats.
Burp Suite Tool
Burp Suite, often referred to as Burp, is a versatile toolkit designed for web application penetration testing.
This tool includes an intercepting proxy that allows users to view and modify the content of requests and responses while they are in transit.
It streamlines the process of sending requests and responses to other tools within Burp Suite, eliminating the need for manual copy-pasting.
The proxy server can be configured to run on a specific loop-back IP address and port, and it can also be customized to filter specific types of request-response pairs.
Why Use Burp Suite in Security Testing
Burp Suite serves as a comprehensive framework for various security testing activities, including:
- Web Crawling: Burp Suite can crawl web applications, systematically exploring their structure.
- Web Application Testing: It facilitates both manual and automated testing of web applications.
- Web Application Analysis: Burp Suite helps analyze the behavior and components of web applications.
- Vulnerability Detection: It helps identify vulnerabilities and security weaknesses in web applications.
Additionally, Burp Suite seamlessly integrates with the Chrome browser, enhancing its usability.
Using Burp Suite in Security Testing
To use Burp Suite in security testing:
- Open Burp and start a new project. Access the proxy settings and open your web browser.
- Burp Suite offers two scanning options: automatic scanning and manual exploration for broader coverage.
- Burp Suite acts as an interceptor between your browser and the web application (cluster). It handles requests (GET) and responses (POST) throughout the cluster’s API.
- Explore all clusters by navigating through each tab and adding items such as VMs, MFA, users, SNMP, policies, protection, recoveries, etc.
- After thoroughly exploring all clusters, initiate an attack using the Active Scan feature.
- The scan typically takes around 1 to 2 hours to complete. Once finished, you can export the scan report.
- Review the Burp report. If there are false positives, you can disregard them. However, if security issues and vulnerabilities are identified, you can flag them for developers through Jira.
View Alerts And Alert Details
Security testing is not just about running tests and scans; it’s also about understanding and acting upon the results.
In our security testing process, the left-hand side of the Footer contains a count of the Alerts found during the test, categorized by risk.
These risk categories serve as a guide to help us prioritize and address vulnerabilities effectively.
These risk categories are: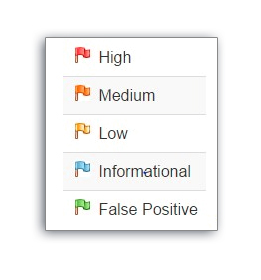
To view the alerts created during your test and delve into their details, follow these steps:
- Click the Alerts tab in the Information Window: This is where you’ll find an overview of all the alerts detected during the security testing process. They are organized or sorted according to their level of risk.
- Click each alert displayed in that window: By clicking on a specific alert, you can access more detailed information. On the right side of the Information Window, you’ll see the URL associated with the alert and the specific vulnerability that was detected.
- In the Workspace Windows, click the Response tab: To gain a deeper understanding of the alert and its context, navigate to the Response tab. Here, you can view the contents of the header and body of the response associated with the alert. This allows you to pinpoint the exact part of the response that generated the alert, helping you assess and address the issue more effectively.
Exploring An Application Manually
While automated security testing tools are invaluable, sometimes manual exploration is necessary to uncover vulnerabilities that automated tools might miss.
Here’s how you can manually explore your application:
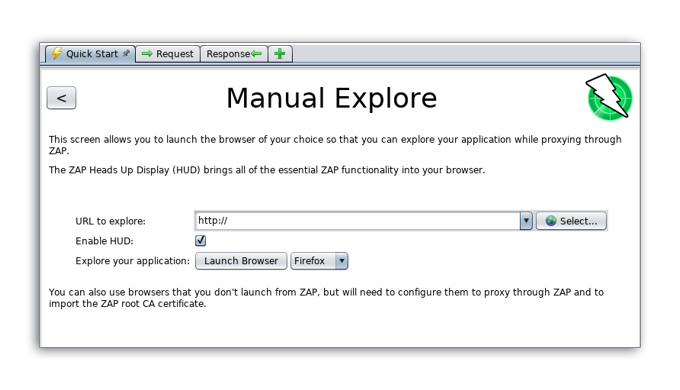
- Start ZAP: To begin manual exploration, open ZAP (Zed Attack Proxy) and navigate to the Quick Start tab in the Workspace Window.
- Click the large Manual Explore button: This initiates the manual exploration process.
- In the URL to explore text box, enter the full URL of the web application: Specify the web application you want to explore manually.
- Select the browser you would like to use: Choose your preferred web browser for manual exploration.
- Click the Launch Browser button: This will open the specified web application in your chosen browser, allowing you to interact with it as a user would.
Forensics Tool
Forensics Tool is a special software developed for advanced data management solutions.
It helps gather logs and important data from a local computer system so that experts can investigate digital issues.
Here’s what it does:
- Provides detailed insights into user actions, including logins and command usage.
- Vigilantly monitors for any potentially malicious activities, such as password alterations.
- Detects and lists active network connections, secure shell logins, and alterations to files and data.
Installation
To install the tool, follow these steps:
- Download the package to one of the nodes using scp or wget.
- Use allscp.sh to transfer the RPM to all nodes of the cluster (allscp.sh <rpm-package-location> /tmp).
- Install the RPM package on all nodes using allssh.sh ‘sudo rpm -U /tmp/<rpm-package-name>’.
Execution
The tool requires execution with sudo privileges. Otherwise, it will fail with an error.
Example:
[-node-1 ~]$ sudo ./forensics/crux/bin/forensics_exec -h
Copying Results
The tool generates a .tgz bundle at the path specified by the ‘output_dir’ parameter, which is typically stored in “timecapsules.”
Uninstall and Cleanup
To uninstall the tool on all nodes and clean up:
Forensics bundles are stored in either “timecapsules” or “output_dir” as specified by the user. Users can copy the .tgz bundle remotely using scp. Afterwards, they can clean up the bundle on the node. The tool does not automatically clean up previous bundles to prevent accidental deletion of important forensics.
To uninstall the tool on all nodes, use the following command:
# Uninstalling the tool
# The RPM name can be found using the “rpm -qa” command.
allssh.sh ‘sudo rpm -e <rpm-name>’
To delete the RPM package from all nodes (if it was copied to /tmp on all nodes), use the following command:
allssh.sh ‘rm /tmp/<rpm-package-name>’
Data stored in each directory are as follows:
- Software Directory:
-
- Contains changes to device protos (UserProto and ConfigProto).
- Stores metadata related to software, including binaries and config files.
- DataBackupIntegrity Directory:
-
- Captures information about the stability of data processes.
- LinuxSW Directory:
-
- Tracks the integrity of files specific to Linux systems using last modified dates and RPM database to detect tampering/modifications.
- LogBundle Directory:
-
- Captures command outputs useful for forensics.
- Preserves system log files with their original directory structure.
- ShellLogins Directory:
-
- Records all shell logins (e.g., ssh, teleport) that occurred within a specified time interval.
- UserActivity Directory:
-
- Captures user activities, including host shell interactions.
- Logs IRIS CLI command history for a specific node.
- NodeAnalysis.csv:
-
- Contains information about suspicious events found in log files for a specific node.
Note: This Forensics Tool is intended for use by SREs (Site Reliability Engineers) and in support cases, particularly for ransomware forensic investigations.
Improving Quality and Delivering Secure Products to Our Customers Through Security Testing Tools
In today’s digital age, ensuring the security of systems and customer data is paramount for maintaining trust and loyalty.
Moreover, the increasing threat of cyberattacks and data breaches necessitates proactive measures.
Therefore, ethical hacking is one such measure, enhancing security systems and improving brand trust and customer experience.
Our Commitment to Data Security
Our services are designed with a focus on:
- Confidentiality, Integrity, and Availability: We protect your data comprehensively.
- Privacy and Control: Tenable ensures your privacy and data control in a safe, secure, and compliant cloud environment. Therefore, thousands trust us with their vulnerability data.
Data Security
Tenable goes the extra mile to secure your data:
- Encryption: Data is encrypted in transit and stored using modern methods.
- Data Privacy: Strict access controls and anonymization protect your data.
Service Reliability
We ensure 99.95% uptime, guarding against disruptions and attacks. Regular automated scans help detect vulnerabilities early.
Proactive Security Measures
We conduct regular automated web application scans on our products to identify and address bugs, exploits, and vulnerabilities early in development.
Customer Data Protection
Each customer’s data is uniquely identified with a “container ID” corresponding to their specific subscription. Moreover, this ensures that access to customer data is strictly limited to the respective customer.
What are the Consequences of Not Conducting Proper Security Testing?
1. Website Vulnerabilities
Websites store valuable data like personal information and business strategies. In addition, neglecting security testing can lead to data breaches, slowdowns, or corruption due to malicious attacks. Moreover, third-party vendors with access can also pose risks.
2. Source Code Exposure
Failure to secure your source code can result in theft and resale by threat actors, potentially harming your company’s competitiveness.
3. Ransomware Attacks
Without security measures, your data may be vulnerable to ransomware, causing application downtime and potential financial losses. Moreover, threat actors also offer ransomware services to others.
4. Financial Records at Risk
Stolen financial records can lead to stock manipulation, regulatory issues, and damage to investor relations.
5. Costly Downtime
Cyberattacks can disrupt network routes and lead to costly application downtime, impacting customer service and your reputation.
6. Legal Consequences
Neglecting security can result in lawsuits from customers or partners for breach of contract and data loss.
7. Missed Training Opportunities
Without understanding your cybersecurity risks, educating your team on threats like ransomware and social engineering becomes challenging.
8. Ignoring External Vulnerabilities
Failing to assess external network vulnerabilities leaves you exposed to potential threats. Moreover, regular testing provides insights and recommendations.
9. Publicized Data Breaches
A lack of security testing increases the risk of data breaches, leading to fines, lost productivity, and reputational damage.
10. Reputation Damage
A data breach can tarnish your company’s reputation, leading to negative reviews and missed business opportunities.
How Can Security Testing Benefit Your Organization?
1. Protection From External Attacks
Think of it like having a shield around your software or website. Moreover, security testing helps find and fix weak points that hackers might use to break in and cause harm. Moreover, it’s like locking your doors to keep out burglars.
2. Keeps Customer Data Secure And Builds Customer Confidence
Imagine you’re buying something online. You want to be sure that your personal information, like your credit card details, is safe. Thereby, security testing makes sure that this information stays confidential and makes customers feel safe using your software or website.
3. Guaranteed Quality Product
Just like you want a good quality phone or video game, people want software that works well and is safe to use. In addition, security testing helps make sure your software is high-quality and free from problems that could crash it or make it vulnerable to attacks.
4. Increase The Demand For Software
When people hear that your software is secure, they are more likely to want to use it. In addition, it’s like a popular movie everyone wants to see because they know it’s good.
5. Improves Trust From Crucial Investors And Lenders
If you want to start a business or get money to make your software better, investors and lenders need to trust you. Also, when they see that you take security seriously, they are more likely to support your project with money.
6. Boosts Overall Business Growth
A secure software or website helps your business grow. Moreover, more customers, money, and opportunities come your way when people trust what you offer.
Secure Your Digital Future with ThinkPalm’s Expertise
In today’s rapidly changing digital world, where cyber threats are increasing, protecting your software and websites is crucial. On the whole, security testing is not just a good idea; it’s a must.
Think of it as a shield that keeps your digital assets safe and builds trust with your customers.
At ThinkPalm, we specialize in security testing. We have a team of experts and the latest tools to ensure the security of your software.
Also, our proactive approach means we find and fix issues before they become problems, guaranteeing top-notch software quality.
Moreover, when you partner with ThinkPalm, you’re not just securing your digital presence; you’re investing in a future where your software thrives, customers trust you completely, and your business grows rapidly.
Why wait? Secure your digital future with ThinkPalm’s expertise, and let’s start a journey of trust, quality, and growth together.
Author Bio
Praveen Kumar M is a seasoned QA Test Lead at Thinkpalm with 13+ years of experience in Backup and storage domain. He excels with tools like Netbackup, EMC Data Domain, and HP Data Protector. Praveen's roles encompass new hardware qualification, regression testing, firmware upgrades, and performance testing. He also actively imparts knowledge to newly onboarded employees for hardware qualification testing.





