A computer network or data network is a set of points interconnected by communication links for receiving as well as transmitting data. Based on the structure of a business, a network can be as simple as two personal computers connected locally on a network or as complex as the internet.
We employ various methods for sending and receiving data such as telephone, computers and more. Network data can flow through greater mechanisms such as communication software, hardware, PSTN wires, satellite, fiber optics and so on.
Mainframes are used as the most critical servers in the network infrastructure whenever speed and security are essential.
A mainframe (also known as “big iron”) is a high-performance computer used for large-scale computing purposes that require more availability and security than what a smaller-scale machine can offer. A mainframe has redundant features that enable it to deliver 99.99% availability.
Mainframes are used by large organizations as their central transaction processing unit. It provides high accuracy, availability, security and responsiveness.
For example, consumers expect their credit card availability 24 hours a day, 365 days a year. They expect those transactions to be safe and quick. The mainframe is typically designed to satisfy massive concurrent transactions processing at a rate of thousands or more transactions within a second. In practice, the number of transaction interfaces among business partners is much more complex than it seems.
A simple process of cash withdrawal from an automated teller machine (ATM) is much more complicated than it appears. The process begins by inserting the individual’s ATM card and entering a personal identification number (PIN). The verification process is carried out by a computer in the network that compares the information you entered to a database of customers belonging to that financial institution. Electronic messages are generated to access the savings account where the money is held. Then, the current account balance is verified and approved. Finally, a message is sent back to the ATM to approve or refuse the transaction.
The withdrawal transaction triggers secondary transactions to update the appropriate savings accounts – this is usually done in real-time. By the time the requested money is dispensed from the machine, the account balance will be reflected by deducting the withdrawal amount. The process turns out to be much more complex for an out-of-territory withdrawal.
For instance, you use Bank A’s ATM to withdraw money from your account at Bank B. For that, Bank B’s database must be accessible and the account status should get updated. All these events occur as the customer waits in front of the machine. The network and mainframe computers involved must be highly accurate and quick to make sure that the response time is “reasonable” from the customer’s point of view. The successful completion of the transaction depends on various factors such as both banks using compatible network technology to exchange information, the speed of mainframe network and much more.
Mainframe architecture includes a variety of network capabilities. The following details use the mainframe operating system used at IBM, the z/OS operating system as an example. Some of these capabilities include:
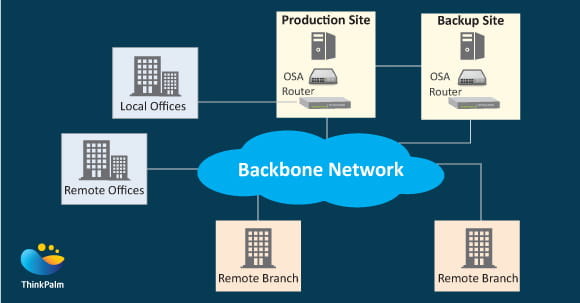
The above figure illustrates a simplified mainframe-based network architecture. The mainframe is connected to external devices using Open Systems Adapter-Express (OSA-Express) which is an integrated LAN Adapter. It is equivalent to a network interface card (NIC) used in Windows and UNIX systems. It supports various protocols and operational modes. OSA-Express card majorly uses the Ethernet protocol, running over copper wire or fiber optic cabling. The I/O systems of mainframe differ from UNIX/Intel systems because of which, OSA card implements advanced technologies required for networking.
For a particular organization, a redundant backbone switch or router is used to connect critical business servers to the primary network. The switch or router provides redundancy by providing more than one physical path to the backbone network. The backbone network is the organization’s high traffic density network.
As expected in every network the Backup site takes care of data processing for planned as well as unplanned outages in the production site. The backup site can provide a data processing site for a very long time. The level and the type of services provided by the backup site is determined by the cost of a backup compared to the cost of failure. Larger the organization, higher is the value placed on the backup site. The backup and the production sites are connected using high-speed connections, normally using fiber optics.
Offices used for computer personnel, administration and back-office services are usually located in the vicinity of the production computer site. These locations may be in the same building, the same campus, or a few blocks away. These sites would be connected using high-speed connections.
Remote sites, such as branch offices and remote offices, are connected to the backbone network. The backbone network normally uses carrier-supplied communication lines. A carrier-supplied network is a network that is provided on behalf of another organization. The speed, the protocol and the topology are designed and implemented by the networking department and the network users.
The z/OS operating system includes a software component called z/OS Communications Server. It implements the SNA and TCP/IP protocols.
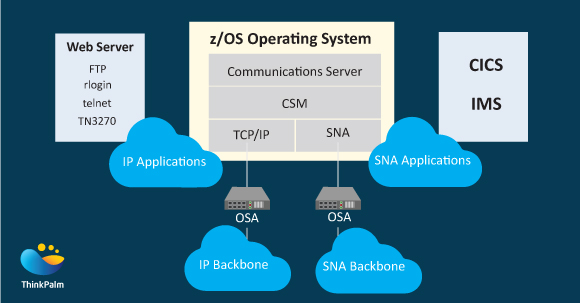
The above figure shows a z/OS Communications Server with three major components, which are:
It is to be noted that z/OS application programmers can exploit various advancements in communications in distinctly different operating systems since TCP/IP, as well as SNA protocols, are implemented in almost all existing platforms.
The mainframe software and hardware are ideally used for network transactions since they are capable of managing huge amounts of data, users and applications simultaneously, without external interference. In networks that support thousands of end-users, the mainframe concepts of data integrity, security and reliability are extended to include the network.
Most z/OS hosts will be located in secure physical locations with strict authorization requirements for employee access. Certain data on such a z/OS host is likely to be considered highly secure. If the data is to be transferred between two z/OS hosts within that secure physical location, the data transfer will most likely be classified as highly secure.
The System Authorization Facility (SAF) interface is a standardized function call available to all applications running on z/OS. The interface call is used to provide quick and controlled authorization, authentication, and logging services. The SAF call is forwarded to an external security manager such as the Resource Access Control Facility (RACF). SAF can collectively restrict end-user capabilities to any organization.
Businesses require their networks to be reliable, always available and fast. They invest a great amount of time and money creating an IT infrastructure that supports these goals – by duplicating hardware and software components, in addition to various other strategies. The extent to which an organization implements a solution depends on availability and performance goals, balanced against the cost of the solution.
The sample configuration below is designed to meet these goals, especially for availability. It illustrates a medium-to-large z/OS data center.
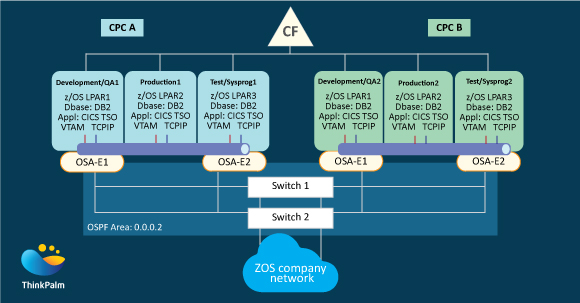
The process is divided physically by central processor complexes and logically by logical partitions.
Other components are
This sample configuration typically indicates that duplicate components are in place to allow scheduled and unscheduled outages and provides the availability that z/OS customers expect.