Did you know that 9 out of 10 web applications contain at least two high-risk vulnerabilities undetected by security testing? Startling but true! In the wake of increasing web application security flaws hindering web application security, Open Web Application Security Project(OWASP), a worldwide not-for-profit charitable organization focused on improving the security of software, has published the OWASP top ten threats against web applications. Below is the list of the major security flaws in a web-based application:
1. Injection
Due to improper coding, hackers can inject SQL commands into database and steal, delete or modify of data .
For example :
If the login checking query is
“select * from TblLogin where UseName='”+txtUserName+“‘and Password='”+txtPassword+“‘ “;
and the hacker is unaware of the user name and password, ‘or 1=1–‘ code is inserted in the username textbox and the password is commented.
“select * from TblLogin where UserName=’‘or1=1–and Password='”+txtPassword+”‘ “;
If the username is known, they can use it with ‘- -‘ as below and the password is commented in query.
“select * from TblLogin where UserName=’‘Admin–‘”+txtPassword+”‘ “;
How to prevent Injection:
- Proper validation of input
- Use Stored procedure instead of inline query
2. Weak Authentication and Session Management
Weak authentication and session management causes security flaws which can be evaded through cookie-based or token-based authentication methods in web application.
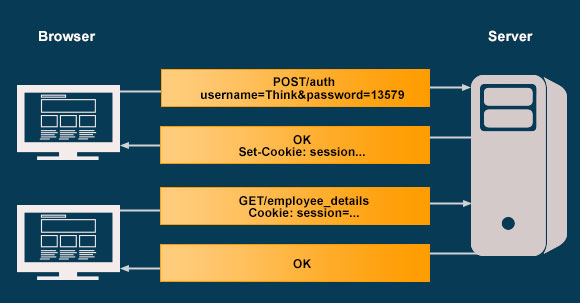
A. Cookie-Based Authentication: In cookie-based authentication, cookies for storing user information are checked during each request. Client posts request to the server that contains user information. Server responds with cookie, which includes the session_id for user identity. The successive server responses verify cookie value before serving the requests.
The limitation of cookie-based authentication is Cross Origin Resource Sharing (CORS). The cookie must be submitted to the server from its origin; cross-origin cookies do not exist preventing accessing resources across different domains.
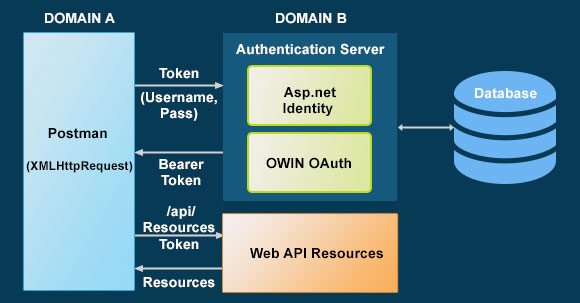
B. Token-Based authentication: Token-based authentication bears tokens between client and server to consume the resources. The client application sends a request to the authentication server with the credentials. If the credentials match, the server sends the token back to the client. Validation happens on every subsequent request against the token. JWT (JSON Web Token) and OWIN OAtuth middleware authentication servers are majorly using for token-based authentication.
3. Insecure Direct Object Reference
In direct object reference, a programmer exposes a reference to an internal implementation of object. A hacker can manipulate direct object reference to access other objects without authorization.
By implementing access control, client requests can be authorized.
4. Security MisConfiguration
Any changes in web config affects the application making the security of web config paramount!
A. Missing Custom Error Handling
Always enable custom error page in web config, otherwise system exception could provide confidential details such as database information to the hacker.
Proper custom error handling method in web config can be realized through:
<customErrors mode=”RemoteOnly” /> <customErrors mode=”On” defaultRedirect=”ErrorPage.htm” />
B. Debugging Enabled
Enabling the Debugging mode is not the proper way to debug information as it helps the hacker. Hence, after deploying the application, the debugging mode should be turned to disabled in web config.
5. Cross-Site Request Forgery (CSRF)
CSRF is an attack that forces an end user to execute unwanted actions on a web application in which they are currently authenticated. For instance, the user logs into www.Mybank.com for funds transfer and without logging out, visits a site that contains malicious images or links. These links may contain scripts hidden from the visitor:
<iframe src=www.Mybank.com/tranfermoney/amout-155&ACNO=98765 />”
If the user clicks an image or link, the malicious code executes. Since the visitor is still logged into www.Mybank.com, the user authentication details are present in the cookie. The request will be processed and the amount will be sent to 98765 account!
A. Prevent CSRF in Net web forms-
- Protect session data using hashing and encryption
- Use SSL for preventing sniffing of session variable and viewstate.
B. Prevent CSRF in Asp.Net in MVC
Use Antiforgery token for preventing CSRF in MVC. Here, when the client requests server page, the server response contains two tokens. One token is sent as cookie and the other one is placed in hidden form field. The tokens are generated randomly due to which the attacker is unable to guess the values in token. The server validates both tokens in the server. If any token is missing in the request, the server disallows the request.
6. Unwanted Redirections and Forwards
Attacker sends E-mail to a user which contains offers related to e-commerce. When the user clicks on the link given, he is redirected to a familiar shopping site (www.shoppingsite.com) that closely relates to the original site (www.shoppig.com). The website might contain a hidden URL like www.shoppingsite.com/login/login?url=”http://malicious.com. When the user enters the credentials, the malicious site displays message invalid credentials. Upon retrying the credentials, the user is redirected to the original shopping site but the credentials are already stolen in this attack!
Prevention method in MVC: If the programmer is using MVC application, they can use Uri.IsLocalUri method
If (Uri.IsLocalUri(returnUrl) )
{
Return Redirect(returnUrl);
}else
{
RedirectToAction(“Index”,”Home:);}
It’s good to incorporate the above mentioned security methods in your application to ensure your systems are not at risk. Stay safe!